I'm a Security Researcher now!
It's come to my attention as a result of the work I did disclosing and posting a proof-of-concept exploit, I have been described as a security researcher (such as in this ZDNet article, or the YouTube video below).
It's a bit of a stretch. I definitely don't consider myself a security researcher or security expert of any kind (although I do think security is extremely important), but it's very flattering to be referred to as such by the likes of Kyle from Huntress Labs.
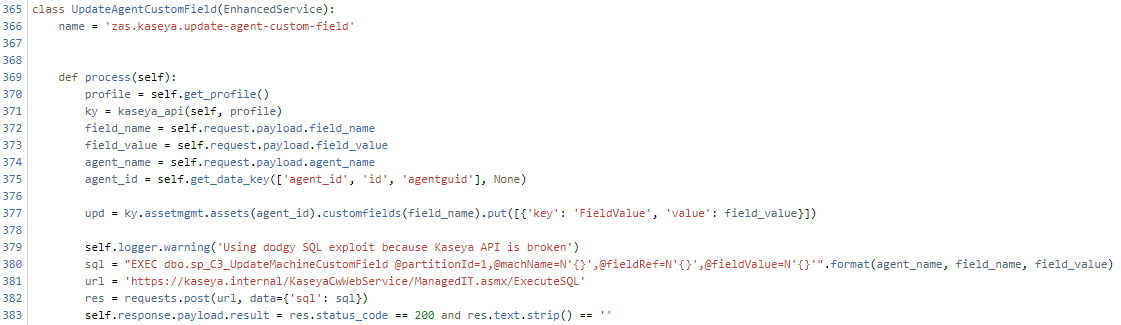
On a related note, the exploit actually came in handy when I needed to automate certain tasks with Kaseya that were not possible with the API:
Ironically the above service is itself vulnerable to SQL injection, if called directly. However, it's only ever called by other services which have already qualified the inputs.
Also worth checking out, the Tradecraft Tuesday podcast from Huntress Labs (which goes into more detail about this exploit, and few other interesting topics):
As to how I feel about an exploit I posted to Github resulting in the compromise of hundreds of organisations... well, that's unfortunate of course but I disclosed the vulnerability responsibly and vendors had plenty of time to warn those who were attacked.
For those wondering if I will look into hunting bug bounties or move into infosec... It's possible. At the moment I don't have the time or skills required, but now that I have a tiny shred of street cred, maybe it's worth looking into.